I’m writing this because I couldn’t find anything specific and definitive that described how this should work and Comcrap used to provide next to nothing on the configuration. This have recently added this.
When you get your setup from Comcrap you’ll get a /30 and another network. We’ll use a /29 in this case. Something like:
Below is your Ips information
LAN IPv4 Block: 50.15.100.24/29
Subnet Mask: 255.255.255.248
Usable Range: 50.15.100.26 - 50.175.100.30
P2P/WAN IPv4: 50.15.100.16/30
Gateway IP: 50.15.100.17
Subnet Mask: 255.255.255.252
Usable Range: 50.15.100.18This is a copy and paste (IPs changed) from the Comcrap welcome email. Poor English and all. So let’s look at what this means. In my case there will be 3 interfaces. WAN, LAN and OPT1. The latter will be where the public IPs are or what Comcrap calls “LAN IPv4 Block.” We’ll start with a basic config of OPNsense. Just run the setup wizard and add the /30 as your WAN interface. In this case you would use 50.15.100.18/30 as your WAN interface IP and 50.15.100.17 as your default gateway. By default the LAN should be up and working after the setup is complete using NAT with 192.168.1.0/24 as the LAN network and OPNsense’s web UI available at 192.168.1.1. Stop here and test your network throughput. Potentially also ask Comcrap for a “RFC2544 Test Birth Certificate.” This is an invasive test that should cover Layer2 and Layer3. If you don’t do this everything else after might be shitty and you won’t know why.
Now the fun part. Add your OPT1 interface, if necessary, and then configure the IPv4 as 50.15.100.25/29 (note this isn’t documented anywhere). Next you’ll need to disable outbound NAT for this subnet. You’ll need to change the mode to “Hybrid outbound NAT rule generation” and then add a new rule with “Do not NAT” checked and use the whole subnet as the source. Comment as necessary. In this case it should look like this when you’re done:
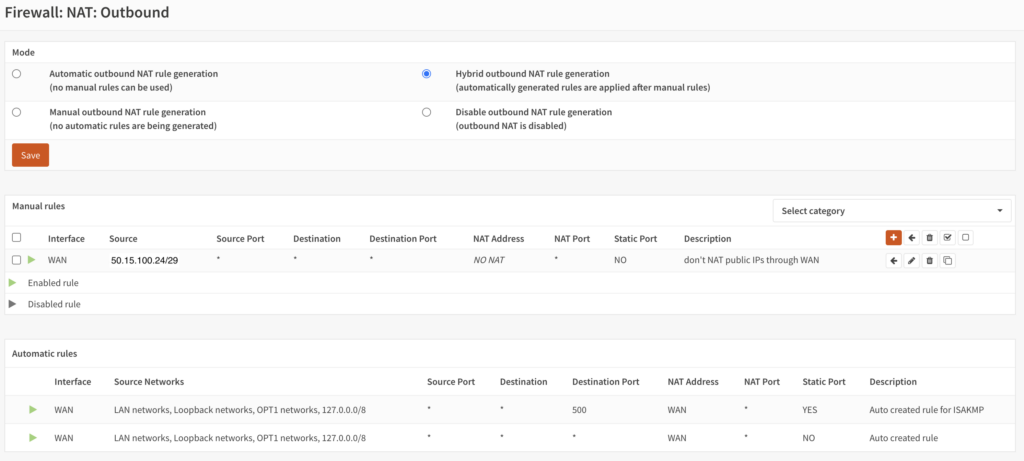
Now we need to look at firewall rules. In this case I’ve setup a host plugged into OPT1 on 50.15.100.26/29. Note that this host’s default gateway is 50.15.100.25, NOT 50.15.100.18 or 50.15.100.17. We’ll create a WAN rule to allow ICMP and SSH into 50.15.100.26/32 (so just that host for now). My rules look like this:
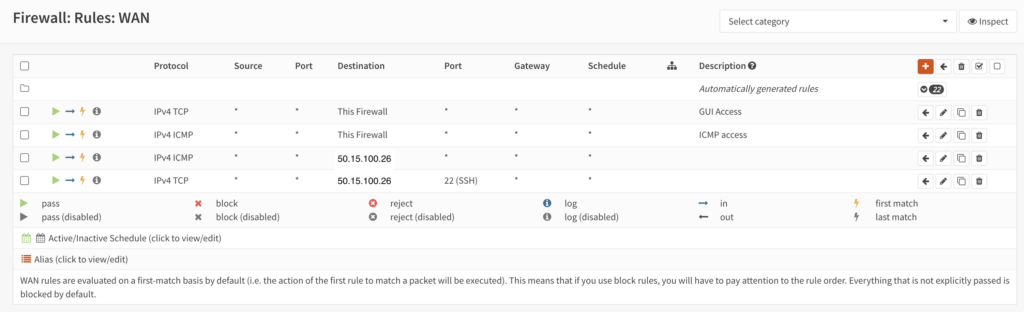
We now have a way for connections to get into 50.15.100.26/32, but that host cannot get out. In this case I’m not looking to manage outbound connections from the 50.15.100.24/29 subnet so I’ll add an inbound rule for the OPT1 interface to let anything in from the OPT1 net (50.15.100.24/29 in this case). This will essentially be the same as the default LAN rule, just on the OPT1 interface and from the OPT1 net. My rule looks like this:
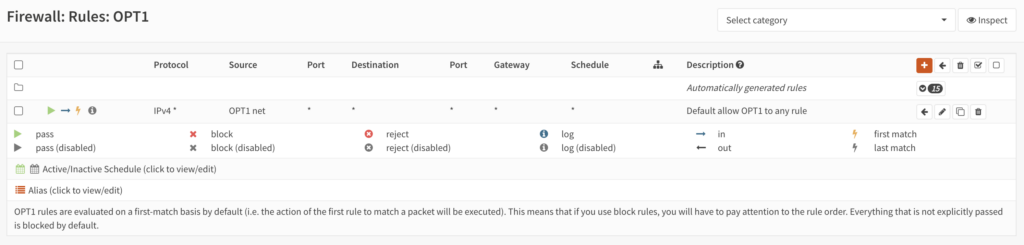
Obviously many changes that can be made here and security should be a major concern if you do this yourself, but I hope this gets you up and going. Or not. I don’t really give a fuck.